This attack technique is used when a Web application is vulnerable to...
Which Steganography technique uses Whitespace to hide secret messages?
This attack uses social engineering techniques to trick users into...
This type of Port Scanning technique splits TCP header into several...
Jason works in the sales and marketing department for a very large...
Jack Hacker wants to break into Brown Co.'s computers and obtain...
TCP SYN Flood attack uses the three-way handshake mechanism.
...
What sequence of packets is sent during the initial TCP three-way...
In Trojan terminology, what is required to create the executable file...
What type of attack is shown in the following diagram?
Lori is a Certified Ethical Hacker as well as a Certified Hacking...
Which of the following type of scanning utilizes automated process of...
Bob waits near a secured door, holding a box. He waits until an...
Which of the following countermeasure can specifically protect against...
Jimmy, an attacker, knows that he can take advantage of poorly...
If a competitor wants to cause damage to your organization, steal...
In TCP communications there are 8 flags; FIN, SYN, RST, PSH, ACK, URG,...
This IDS defeating technique works by splitting a datagram (or packet)...
Web servers often contain directories that do not need to be indexed....
SNMP is a connectionless protocol that uses UDP instead of TCP packets...
Jake works as a system administrator at Acme Corp. Jason, an...
Joel and her team have been going through tons of garbage, recycled...
SYN Flood is a DOS attack in which an attacker deliberately violates...
What is War Dialing?
An attacker finds a web page for a target organization that supplies...
What type of port scan is shown below?
Stephanie works as a records clerk in a large office building in...
Attacking well-known system defaults is one of the most common hacker...
Stephanie works as senior security analyst for a manufacturing company...
In the context of password security: a simple dictionary attack...
An attacker has successfully compromised a remote computer. Which of...
Ursula is a college student at a University in Amsterdam. Ursula...
BankerFox is a Trojan that is designed to steal users' banking...
In the context of Trojans, what is the definition of a Wrapper?
Neil is a network administrator working in Istanbul. Neil wants to...
In what stage of Virus life does a stealth virus gets activated with...
One of the effective DoS/DDoS countermeasures is 'Throttling'....
This tool is widely used for ARP Poisoning attack. Name the tool.
David is a security administrator working in Boston. David has been...
Fake Anti-Virus, is one of the most frequently encountered and...
In which part of OSI model does ARP Poisoning occurs?
What does FIN in TCP flag define?
Steven the hacker realizes the network administrator of Acme...
You are the Security Administrator of Xtrinity, Inc. You write...
Which type of hacker represents the highest risk to your network?
Bret is a web application administrator and has just read that there...
Choose one of the following pseudo codes to describe this statement:
...
Cyber Criminals have long employed the tactic of masking their true...
The following script shows a simple SQL injection. The script builds...
What is a sniffing performed on a switched network called?
Consider the following code:
...
What are the limitations of Vulnerability scanners? (Select 2 answers)
How does traceroute map the route a packet travels from point A to...
More sophisticated IDSs look for common shellcode signatures. But even...
What is the problem with this ASP script (login.asp)?
Which of the following tools would be considered a Signature Integrity...
Google uses a unique cookie for each browser used by an individual...
Attackers target HINFO record types stored on a DNS server to...
You are the security administrator of Jaco Banking Systems located in...
Anonymizer sites access the Internet on your behalf, protecting your...
Bob has set up three web servers on Windows Server 2008 IIS 7.0. Bob...
Dan is conducting penetration testing and has found a vulnerability in...
What port number is used by Kerberos protocol?
Attackers footprint target Websites using Google Hacking techniques....
Syslog is a standard for logging program messages. It allows...
Lori was performing an audit of her company's internal Sharepoint...
TCP/IP Session Hijacking is carried out in which OSI layer?
You want to hide a secret.txt document inside...
While performing a ping sweep of a local subnet you receive an ICMP...
You receive an e-mail with the following text message.
...
Peter extracts the SID list from Windows 2008 Server machine using the...
What type of session hijacking attack is shown in the exhibit?
You run nmap port Scan on 10.0.0.5 and attempt to gain banner/server...
A rootkit is a collection of tools (programs) that enable...
Which of the following statements would NOT be a proper definition for...
A common technique for luring e-mail users into opening...
What does ICMP (type 11, code 0) denote?
Vulnerability scanners are automated tools that are used to identify...
Jayden is a network administrator for her company. Jayden wants to...
Your computer is infected by E-mail tracking and spying Trojan. This...
Annie has just succeeded in stealing a secure cookie via a XSS attack....
Which type of scan does NOT open a full TCP connection?
In Buffer Overflow exploit, which of the following registers gets...
Shayla is an IT security consultant, specializing in social...
How do you defend against DHCP Starvation attack?
You want to capture Facebook website traffic in Wireshark. What...
What file system vulnerability does the following command take...
How many bits encryption does SHA-1 use?
Maintaining a secure Web server requires constant effort, resources,...
What type of Virus is shown here?
What is the correct command to run Netcat on a server using port 56...
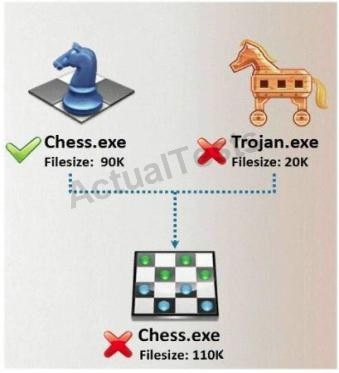
What type of Trojan is this?
XSS attacks occur on Web pages that do not perform appropriate bounds...
How would you describe an attack where an attacker attempts to deliver...
Most cases of insider abuse can be traced to individuals who are...
How do you defend against ARP Spoofing? Select three.
You just purchased the latest DELL computer, which comes pre-installed...
How do you defend against Privilege Escalation? (Choose all that...
The SYN flood attack sends TCP connections requests faster than a...
Which of the following statement correctly defines ICMP Flood Attack?...