CCENT Practice Certification Exam 2
A CCENT certification is one thing that every IT personnel know is able to help them show their competency to a prospective employer. Are you studying to take the certification exam and are not sure about your readiness? Take up the practice questions below and get a view of what to expect.
- 1.
Data is being sent from a source PC to a destination server. Which three statements correctly describe the function of TCP or UDP in this situation? (Choose three.)
- A.
The UDP destination port number identifies the application or service on the server which will handle the data.
- B.
TCP is the preferred protocol when a function requires lower network overhead.
- C.
UDP segments are encapsulated within IP packets for transport across the network.
- D.
The source port field identifies the running application or service that will handle data returning to the PC.
- E.
The TCP source port number identifies the sending host on the network
- F.
The TCP process running on the PC randomly selects the destination port when establishing a session with the server.
Correct Answer(s)
A. The UDP destination port number identifies the application or service on the server which will handle the data.
C. UDP segments are encapsulated within IP packets for transport across the network.
D. The source port field identifies the running application or service that will handle data returning to the PC.Explanation
TCP and UDP are both transport layer protocols used for sending data from a source PC to a destination server.
The statement "The UDP destination port number identifies the application or service on the server which will handle the data" is correct. In UDP, the destination port number is used to identify the specific application or service on the server that should receive the data.
The statement "UDP segments are encapsulated within IP packets for transport across the network" is also correct. UDP segments are encapsulated within IP packets, which allows them to be transported across the network.
The statement "The source port field identifies the running application or service that will handle data returning to the PC" is the third correct statement. The source port field in both TCP and UDP identifies the application or service on the source PC that is responsible for handling the data returning from the server.Rate this question:
-
- 2.
In what two situations would UDP be the preferred transport protocol over TCP? (Choose two.)
- A.
When applications need to guarantee that a packet arrives intact, in sequence, and unduplicated
- B.
When a faster delivery mechanism is needed
- C.
When delivery overhead is not an issue
- D.
When applications do not need to guarantee delivery of the data
- E.
When destination port numbers are dynamic
Correct Answer(s)
B. When a faster delivery mechanism is needed
D. When applications do not need to guarantee delivery of the dataExplanation
UDP would be the preferred transport protocol over TCP when a faster delivery mechanism is needed because UDP does not have the same level of reliability and error-checking mechanisms as TCP, which allows for faster transmission. Additionally, UDP would be preferred when applications do not need to guarantee delivery of the data because UDP does not have the same level of error recovery and retransmission capabilities as TCP, making it more suitable for applications where occasional data loss is acceptable.Rate this question:
-
- 3.
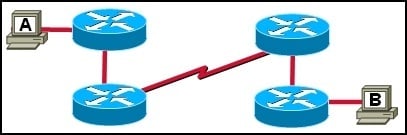
Refer to the exhibit. Workstation A sends an IP packet to workstation B. Which two statements describe the encapsulation of the packet as it passes through the network?
- A.
The Layer 2 header is stripped from the packet by each router.
- B.
The destination Layer 2 address of the packet does not change
- C.
The source Layer 3 address of the packet changes at each router.
- D.
The Layer 2 header changes at each router
- E.
The Layer 3 header is stripped from the packet by each router
Correct Answer(s)
A. The Layer 2 header is stripped from the packet by each router.
D. The Layer 2 header changes at each routerExplanation
As the IP packet passes through each router in the network, the Layer 2 header is stripped from the packet by each router. This means that each router removes the Layer 2 header before forwarding the packet to the next router. Additionally, the Layer 2 header changes at each router. This means that each router adds its own Layer 2 header with the appropriate source and destination addresses before forwarding the packet to the next router.Rate this question:
-
- 4.
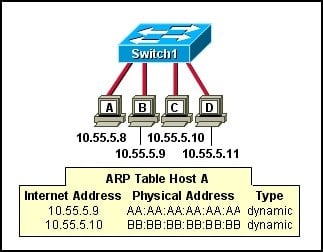
Refer to the exhibit. A switch with a default configuration connects four hosts. The ARP table for host A is shown. What happens when host A wants to send an IP packet to host D?
- A.
Host A sends an ARP request to the MAC address of host D
- B.
Host D sends an ARP request to host A.
- C.
Host A sends out the packet to the switch. The switch sends the packet only to the host D, which in turn responds
- D.
Host A sends out a broadcast of FF:FF:FF:FF:FF:FF. Every other host connected to the switch receives the broadcast and host D responds with its MAC address.
Correct Answer
D. Host A sends out a broadcast of FF:FF:FF:FF:FF:FF. Every other host connected to the switch receives the broadcast and host D responds with its MAC address.Explanation
When host A wants to send an IP packet to host D, it sends out a broadcast message with the MAC address FF:FF:FF:FF:FF:FF. This broadcast message is received by every other host connected to the switch. Host D, being the intended recipient, responds to the broadcast message with its MAC address. This allows host A to know the MAC address of host D, which is necessary for the packet to be properly delivered.Rate this question:
-
- 5.
What three services are provided by the transport layer? (Choose three.)
- A.
Flow control
- B.
Encryption of data
- C.
Path determination
- D.
Connection establishment
- E.
Error recovery
- F.
Bit transmission
- G.
Data representation
Correct Answer(s)
A. Flow control
D. Connection establishment
E. Error recoveryExplanation
The transport layer provides three services: flow control, connection establishment, and error recovery. Flow control ensures that the sender does not overwhelm the receiver with too much data, preventing congestion. Connection establishment sets up a reliable communication channel between the sender and receiver. Error recovery detects and retransmits lost or corrupted data to ensure reliable delivery.Rate this question:
-
- 6.
Which layer of the OSI model handles the process of identifying and discarding damaged frames?
- A.
Presentation
- B.
Session
- C.
Transport
- D.
Network
- E.
Data link
- F.
Physical
Correct Answer
E. Data linkExplanation
The data link layer of the OSI model handles the process of identifying and discarding damaged frames. This layer is responsible for error detection and correction, ensuring that data is transmitted without errors over the physical network. It checks the integrity of the frames by using techniques such as checksums or cyclic redundancy checks (CRC). If a frame is found to be damaged, it is discarded and not passed on to the network layer for further processing.Rate this question:
-
- 7.
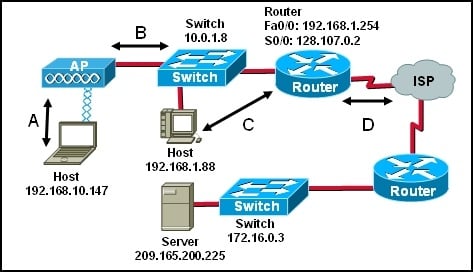
Refer to the exhibit. Considering the information that follows and the exhibit, where is the data flowing? Source IP address: 192.168.1.88 Destination IP address: 209.165.200.225 Source MAC address: 00-11-12-7a-41-10 Destination MAC address: 00-0d-cc-f4-ad-2c Source Port: 1464 Destination Port: 23
- A.
A – from laptop to access point
- B.
B – from access point to attached switch
- C.
C – from host to default gateway router
- D.
D – from router to ISP
Correct Answer
C. C – from host to default gateway routerExplanation
The data is flowing from the host (laptop) to the default gateway router. This can be determined by looking at the source and destination IP addresses. The source IP address is 192.168.1.88, which is the IP address of the laptop. The destination IP address is 209.165.200.225, which is the IP address of the default gateway router. Therefore, the data is flowing from the host to the default gateway router.Rate this question:
-
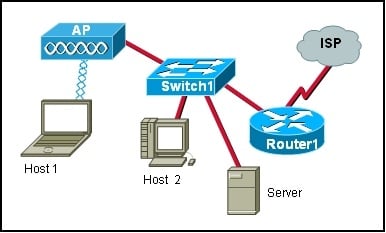
- 8.
Refer to the exhibit. If Host 1 needs to request its IP address from the server, what protocol would be used to process that request?
- A.
CSMA/CD
- B.
CSMA/CA
- C.
DHCP
- D.
ICMP
- E.
NAT
- F.
FTP
Correct Answer
C. DHCPExplanation
DHCP (Dynamic Host Configuration Protocol) is used to automatically assign IP addresses to devices on a network. In this scenario, Host 1 needs to request its IP address from the server, which is the role of DHCP.Rate this question:
-
- 9.
Refer to the exhibit. If Host 1 were to transfer a file to the server, what layers of the TCP/IP model would be used?
- A.
Only application and Internet layers
- B.
Only Internet and network access layers
- C.
Only application, Internet, and network access layers
- D.
Application, transport, Internet, and network access layers
- E.
Only application, transport, network, data link, and physical layers
- F.
Application, session, transport, network, data link, and physical layers
Correct Answer
D. Application, transport, Internet, and network access layersExplanation
The correct answer is application, transport, Internet, and network access layers. When Host 1 transfers a file to the server, the application layer is responsible for initiating the file transfer. The transport layer ensures reliable delivery of the file by dividing it into smaller packets and managing their transmission. The Internet layer handles the addressing and routing of the packets over the network. Finally, the network access layer is responsible for transmitting the packets over the physical network medium.Rate this question:
-
- 10.
ABC company needs to connect its router to an ISP to access the Internet. What device is needed to connect the router to the ISP if the ISP supplies a T1 leased line for the connection?
- A.
CSU/DSU
- B.
Modem
- C.
DSL router
- D.
NT1 device
- E.
ISDN modem
Correct Answer
A. CSU/DSUExplanation
The correct answer is CSU/DSU. A CSU/DSU (Channel Service Unit/Data Service Unit) is needed to connect the router to the ISP when a T1 leased line is supplied. A CSU/DSU is responsible for converting the digital data from the router into a format that can be transmitted over the T1 leased line and vice versa. It provides the necessary interface between the router and the leased line. A modem, DSL router, NT1 device, or ISDN modem would not be suitable for this type of connection.Rate this question:
-
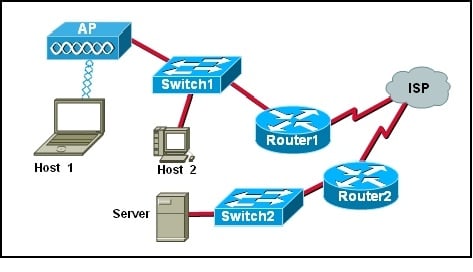
- 11.
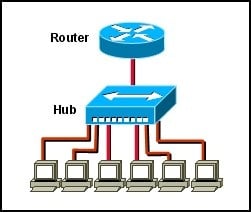
Refer to the exhibit. How many collision domains exist in the exhibited network?
- A.
1
- B.
2
- C.
3
- D.
6
- E.
7
Correct Answer
A. 1Explanation
In the exhibited network, there is only one collision domain. A collision domain is a network segment where collisions can occur between devices that are connected to the same physical medium, such as a hub or a shared Ethernet cable. In this case, there is only one connection point or physical medium shown in the exhibit, indicating that there is only one collision domain.Rate this question:
-
- 12.
What are two actions performed by a Cisco switch? (Choose two.)
- A.
Building a routing table that is based on the first IP address in the frame header
- B.
Using the source MAC addresses of frames to build and maintain a MAC address table
- C.
Forwarding frames with unknown destination IP addresses to the default gateway
- D.
Utilizing the MAC address table to forward frames via the destination MAC address
- E.
Examining the destination MAC address to add new entries to the MAC address table
Correct Answer(s)
B. Using the source MAC addresses of frames to build and maintain a MAC address table
D. Utilizing the MAC address table to forward frames via the destination MAC addressExplanation
A Cisco switch performs two actions. First, it uses the source MAC addresses of frames to build and maintain a MAC address table. This table keeps track of which devices are connected to which ports on the switch. Second, the switch utilizes the MAC address table to forward frames to the appropriate destination MAC address. By referencing the table, the switch can determine the correct port to send the frame to, ensuring efficient and accurate forwarding of network traffic.Rate this question:
-
- 13.
A network administrator wants to configure a Cisco 2960 switch so that access to each switch port is limited to one MAC address. What will accomplish the administrator’s objective?
- A.
Cisco Discovery Protocol
- B.
Port security
- C.
Internet Control Message Protocol
- D.
Access lists
- E.
Flow control
Correct Answer
B. Port securityExplanation
Port security is a feature in Cisco switches that allows the network administrator to restrict access to each switch port to a specific MAC address. By enabling port security, the switch will only allow network traffic from the MAC address that is associated with that port. This helps to prevent unauthorized devices from connecting to the network and enhances network security.Rate this question:
-
- 14.
When would you want to use the switchport port-security mac-address sticky command?
- A.
Whenever you need to protect an unused switch port
- B.
Whenever you want the port to only allow a single host device to connect
- C.
Whenever you need the port to recognize the statically assigned MAC address in the MAC address table
- D.
Whenever multiple devices share the same port
Correct Answer
D. Whenever multiple devices share the same portExplanation
The switchport port-security mac-address sticky command should be used whenever multiple devices share the same port. This command allows the switch to dynamically learn the MAC addresses of the devices connected to the port and automatically adds them to the port-security configuration. This ensures that only the learned MAC addresses are allowed to connect to the port, preventing unauthorized devices from accessing the network.Rate this question:
-
- 15.
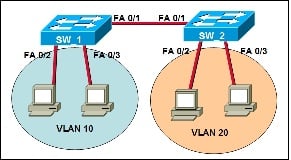
Refer to the exhibit. SW_1 and SW_2 have been configured with VLAN10 and VLAN20. The two switches are connected by a trunking link. During testing, workstations on the same VLAN can ping each other, but workstations on the opposite VLAN cannot ping each other. What needs to be done to fix the problem?
- A.
Configure VTP on both switches so they can share VLAN information.
- B.
Assign a management VLAN on each switch with IP addresses in the same subnet.
- C.
Configure an access port on each switch.
- D.
Add a Layer 3 device to the network.
Correct Answer
D. Add a Layer 3 device to the network.Explanation
The problem is that workstations on different VLANs cannot ping each other. This indicates that there is no inter-VLAN routing happening between the VLANs. To fix this issue, a Layer 3 device such as a router or a Layer 3 switch needs to be added to the network. This device will be able to route traffic between the VLANs, allowing workstations on different VLANs to communicate with each other.Rate this question:
-
- 16.
When configuring a switch to use SSH for virtual terminal connections, what is the purpose of the crypto key generate rsa command?
- A.
Show SSH connected hosts
- B.
Disconnect SSH connected hosts
- C.
Create a public and private key pair
- D.
Show active SSH ports on the switch
- E.
Access the SSH database configuration
Correct Answer
C. Create a public and private key pairExplanation
The purpose of the "crypto key generate rsa" command is to create a public and private key pair. This key pair is essential for establishing a secure SSH connection between the switch and other devices. The public key is used for encryption, while the private key is kept secret and used for decryption. This command generates both keys, allowing for secure communication over SSH.Rate this question:
-
- 17.
Which three statements are true about full-duplex operation on an Ethernet network? (Choose three.)
- A.
There are no collisions in full-duplex mode.
- B.
A dedicated switch port is required for each node.
- C.
Hub ports are preconfigured for full-duplex mode.
- D.
The host network card must detect the availability of the media before transmitting.
- E.
The host network card and the switch port must both be in full-duplex mode.
Correct Answer(s)
A. There are no collisions in full-duplex mode.
B. A dedicated switch port is required for each node.
E. The host network card and the switch port must both be in full-duplex mode.Explanation
In full-duplex mode, there are no collisions because data can be transmitted and received simultaneously. A dedicated switch port is required for each node to allow for simultaneous communication. The host network card and the switch port must both be in full-duplex mode to enable simultaneous data transmission and reception.Rate this question:
-
- 18.
What are three characteristics of CSMA/CD? (Choose three.)
- A.
Devices can be configured with a higher transmission priority.
- B.
A jam signal indicates that the collision has cleared and the media is not busy.
- C.
A device listens and waits until the media is not busy before transmitting.
- D.
The device with the electronic token is the only one that can transmit after a collision
- E.
All of the devices on a segment see data that passes on the network medium.
- F.
After detecting a collision, hosts can attempt to resume transmission after a random time delay has expired.
Correct Answer(s)
C. A device listens and waits until the media is not busy before transmitting.
E. All of the devices on a segment see data that passes on the network medium.
F. After detecting a collision, hosts can attempt to resume transmission after a random time delay has expired.Explanation
CSMA/CD (Carrier Sense Multiple Access with Collision Detection) is a protocol used in Ethernet networks to manage how devices access the network medium. Three characteristics of CSMA/CD are as follows:
1. A device listens and waits until the media is not busy before transmitting: This means that devices will check if the network medium is currently being used by another device before attempting to transmit data. If the media is busy, the device will wait until it becomes available.
2. All of the devices on a segment see data that passes on the network medium: In CSMA/CD, all devices on a network segment can see the data that is being transmitted on the network medium. This allows for shared communication and ensures that all devices receive the transmitted data.
3. After detecting a collision, hosts can attempt to resume transmission after a random time delay has expired: In the event of a collision, where multiple devices attempt to transmit data at the same time and their signals collide, CSMA/CD allows the devices to wait for a random time delay before attempting to transmit again. This helps to reduce the likelihood of another collision occurring.Rate this question:
-
- 19.
Zero
- A.
Q
- B.
W
- C.
Ffg
Correct Answer(s)
A. Q
B. W -
- 20.
Which three addresses are valid public addresses? (Choose three.)
- A.
198.133.219.17
- B.
192.168.1.245
- C.
10.15.250.5
- D.
128.107.12.117
- E.
192.15.301.240
- F.
64.104.78.227
Correct Answer(s)
A. 198.133.219.17
D. 128.107.12.117
F. 64.104.78.227Explanation
The three valid public addresses are 198.133.219.17, 128.107.12.117, and 64.104.78.227. These addresses are valid because they are within the range of public IP addresses, which are used to identify devices on the internet. The other addresses, 192.168.1.245, 10.15.250.5, and 192.15.301.240, are private addresses that are used for internal networks and cannot be directly accessed from the internet.Rate this question:
-
- 21.
Refer to the exhibit. Four hosts are being added to the 172.16.112.0 network. Which IP address is invalid as a host address for this network?
- A.
172.16.113.55
- B.
172.16.112.255
- C.
172.16.127.255
- D.
172.16.112.89
- E.
172.16.120.96
Correct Answer
C. 172.16.127.255Explanation
The given IP address 172.16.127.255 is invalid as a host address for the network 172.16.112.0 because it falls outside the range of valid host addresses for the network. The network 172.16.112.0 has a subnet mask that allows for a maximum of 254 host addresses (excluding the network and broadcast addresses). Therefore, any IP address above 172.16.112.254 is considered invalid for host assignment.Rate this question:
-
- 22.
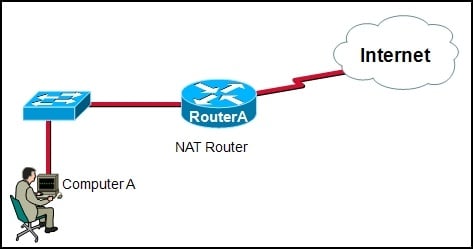
Refer to the exhibit. Using PAT, RouterA is configured to translate all private inside addresses to a single public address. The network administrator wants to determine which port number is being used in the translation of the ComputerA inside private IP address. Which command could be used if the administrator sits at ComputerA but is not allowed remote access to RouterA?
- A.
Ipconfig /all
- B.
Traceroute
- C.
Netstat
- D.
Tracert
Correct Answer
C. NetstatExplanation
The netstat command can be used to display the active network connections and listening ports on a computer. By running netstat on ComputerA, the network administrator can see the port number being used in the translation of the inside private IP address.Rate this question:
-
- 23.
What type of address is 172.16.134.64 with the subnet mask 255.255.255.224?
- A.
This is a usable host address.
- B.
This is a broadcast address.
- C.
This is a network address.
- D.
This is an Internet-routable address.
Correct Answer
C. This is a network address.Explanation
The given IP address 172.16.134.64 with the subnet mask 255.255.255.224 falls within the range of a network address. The subnet mask 255.255.255.224 indicates that the first 27 bits of the IP address are used to identify the network, while the remaining 5 bits are used for host addresses. Therefore, the IP address 172.16.134.64 is the network address for the network it belongs to.Rate this question:
-
- 24.
The router reads each bit to determine the class of an address. Which three series of binary numbers would the router identify as public Class C addresses? (Choose three.)
- A.
10101100.00100000.00010001.00010111
- B.
11000110.10000101.11011011.01010111
- C.
11010001.10100101.11001000.11101101
- D.
11000000.10101000.00100000.01000000
- E.
11000000.00011111.00000111.10111011
Correct Answer(s)
B. 11000110.10000101.11011011.01010111
C. 11010001.10100101.11001000.11101101
E. 11000000.00011111.00000111.10111011 -
- 25.
Given a host with the IP address 192.168.65.54 and a subnet mask of 255.255.255.240, to which network does the host belong?
- A.
192.168.65.16
- B.
192.168.65.32
- C.
192.168.65.48
- D.
192.168.65.64
Correct Answer
C. 192.168.65.48Explanation
The given IP address 192.168.65.54 and subnet mask 255.255.255.240 indicate that the network portion of the IP address is obtained by performing a bitwise AND operation between the IP address and the subnet mask. The result is 192.168.65.48, which is the network address to which the host belongs.Rate this question:
-
- 26.
Refer to the exhibit. Which IP address can be assigned to the default gateway for host A?
- A.
10.184.0.1
- B.
10.192.0.0
- C.
10.199.255.254
- D.
10.200.255.254
Correct Answer
C. 10.199.255.254Explanation
The IP address 10.199.255.254 can be assigned to the default gateway for host A because it falls within the same network range as the IP address of host A. The default gateway is responsible for routing network traffic between different networks, so it needs to have an IP address within the same network as the host.Rate this question:
-
- 27.
Refer to the exhibit. What would be a valid network address for the new subnet on RTA?
- A.
10.16.10.16/28
- B.
10.16.10.24/28
- C.
10.16.10.30/28
- D.
10.16.10.56/28
- E.
10.16.10.72/28
Correct Answer
A. 10.16.10.16/28Explanation
The given IP addresses are all in the same subnet, which has a subnet mask of /28. The valid network address for this subnet would be the first IP address in the range, which is 10.16.10.16. This is because the subnet mask of /28 allows for a total of 16 IP addresses, so the network address would be the first IP in that range.Rate this question:
-
- 28.
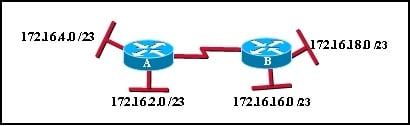
Refer to the exhibit. The network shown is using classful subnetting. The serial link between routers A and B is configured with addresses from the 172.16.6.0/23 subnet. How many valid IP addresses are wasted on this subnetwork?
- A.
252
- B.
254
- C.
256
- D.
508
- E.
510
- F.
512
Correct Answer
D. 508Explanation
In classful subnetting, a /23 subnet has a total of 512 IP addresses. However, the network in the exhibit is only using addresses from the 172.16.6.0/23 subnet for the serial link between routers A and B. This means that the remaining IP addresses in the subnet are wasted and not being utilized. Therefore, the number of valid IP addresses wasted on this subnetwork is 508.Rate this question:
-
- 29.
What are three valid host addresses given a subnet mask of 255.255.254.0? (Choose three.)
- A.
64.100.2.255
- B.
172.55.33.255
- C.
64.104.129.0
- D.
192.168.162.255
- E.
10.165.55.255
- F.
128.107.62.0
Correct Answer(s)
A. 64.100.2.255
C. 64.104.129.0
D. 192.168.162.255 -
- 30.
Refer to the exhibit. Which two interfaces could be used for a leased-line WAN connection? (Choose two.)
- A.
A
- B.
B
- C.
C
- D.
D
- E.
E
- F.
F
Correct Answer(s)
A. A
B. BExplanation
The correct answer is a and b. Interfaces a and b could be used for a leased-line WAN connection.Rate this question:
-
- 31.
What type of cable is used for connectivity between a model 2620 router and a model 2950 switch (point A), a model 2950 switch and a model 1900 switch (point B), and a model 2950 switch and a host (point C)?
- A.
A – straight-through; B – rollover; C – straight-through
- B.
A – crossover; B – straight-through; C – straight-through
- C.
A – straight-through; B – straight-through; C – crossover
- D.
A – crossover; B – straight-through; C – crossover
- E.
A – straight-through; B – crossover; C – straight-through
- F.
A – straight-through; B – crossover; C – crossover
Correct Answer
E. A – straight-through; B – crossover; C – straight-throughExplanation
The correct answer is A – straight-through; B – crossover; C – straight-through. A straight-through cable is used for connectivity between a router and a switch, as well as between a switch and a host. This type of cable has the same pin configuration on both ends, allowing for communication between devices on the same network. However, when connecting two switches together, a crossover cable is needed. This type of cable has a different pin configuration on each end, allowing for proper communication between the switches.Rate this question:
-
- 32.
Refer to the exhibit. A small business has asked for advice about what type of cable will be needed to connect their modular routers. What type of connector is used by each device that is shown?
- A.
WIC-2T is a DB60 connector, WIC1T is a Smart Serial connector, and WIC-1ENET is an RJ45 connector.
- B.
WIC-2T is an RJ45 connector, WIC1T is a DB60 connector, and WIC-1ENET is a Smart Serial connector.
- C.
WIC-2T is a DB60 connector, WIC1T is a Smart Serial connector, and WIC-1ENET is an RJ45 connector.
- D.
WIC-2T is a Token Ring connector, WIC1T is a DB25 connector, and WIC-1ENET is an RJ11 connector.
- E.
WIC-2T is a Smart Serial connector, WIC1T is a DB60 connector, and WIC-1ENET is an RJ45 connector.
Correct Answer
E. WIC-2T is a Smart Serial connector, WIC1T is a DB60 connector, and WIC-1ENET is an RJ45 connector.Explanation
The given correct answer states that WIC-2T is a Smart Serial connector, WIC1T is a DB60 connector, and WIC-1ENET is an RJ45 connector. This means that the WIC-2T device uses a Smart Serial connector, the WIC1T device uses a DB60 connector, and the WIC-1ENET device uses an RJ45 connector.Rate this question:
-
- 33.
Refer to the exhibit. The router that is named myhome has received a frame from the host 192.168.254.7. The contents of this frame are being sent to host 172.16.14.243. What is the Layer 2 destination address of the frame as it leaves the myhome router?
- A.
0008.a3b6.ce05
- B.
0009.1281.18a8
- C.
000a.8a47.e612
- D.
172.16.14.129
- E.
172.16.14.243
- F.
192.168.254.7
Correct Answer
A. 0008.a3b6.ce05Explanation
The Layer 2 destination address of the frame as it leaves the myhome router is 0008.a3b6.ce05.Rate this question:
-
- 34.
Why is it important for the router to maintain an accurate routing table?
- A.
To provide Layer 2 addressing information for the next hop
- B.
To prevent broadcasts from occurring on the LAN
- C.
To determine the best path to the destination network
- D.
To identify all of the routers in a network
Correct Answer
C. To determine the best path to the destination networkExplanation
It is important for the router to maintain an accurate routing table in order to determine the best path to the destination network. The routing table contains information about the available networks and the paths to reach them. By maintaining an accurate routing table, the router can make informed decisions about which path to choose for forwarding packets. This helps in efficient and reliable routing of data across the network.Rate this question:
-
- 35.
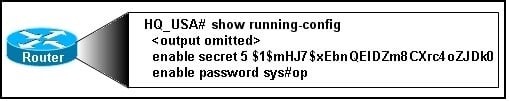
Refer to the exhibit. Based on the exhibited router output, what two conclusions can be made? (Choose two.)
- A.
The enable password has been encrypted.
- B.
The service password-encryption command has not been added to the configuration.
- C.
The passwords that are shown restrict access to the router console.
- D.
The password that will gain access to privileged mode is sys#op.
- E.
The passwords that are shown will be required to enter privileged EXEC mode on this router.
Correct Answer(s)
B. The service password-encryption command has not been added to the configuration.
E. The passwords that are shown will be required to enter privileged EXEC mode on this router.Explanation
Based on the exhibited router output, two conclusions can be made. First, the service password-encryption command has not been added to the configuration because the passwords are displayed in plain text. Second, the passwords that are shown will be required to enter privileged EXEC mode on this router, as indicated by the "enable secret" and "line console 0" commands.Rate this question:
-
- 36.
What would be a common reason to upgrade from RIPv1 to RIPv2?
- A.
RIPv2 takes less router memory than RIPv1 takes.
- B.
RIPv2 supports a larger network (more routers) than RIPv1 supports.
- C.
RIPv2 supports discontiguous networks and RIPv1 does not.
- D.
RIPv2 supports classless routing. RIPv1 is classful
Correct Answer
D. RIPv2 supports classless routing. RIPv1 is classfulExplanation
RIPv2 supports classless routing, which means it can support variable length subnet masks (VLSM) and route summarization. This allows for more efficient use of IP address space and more flexibility in network design. On the other hand, RIPv1 is classful and does not support these features. Therefore, upgrading from RIPv1 to RIPv2 would be beneficial for organizations that require more advanced routing capabilities and need to accommodate larger or more complex networks.Rate this question:
-
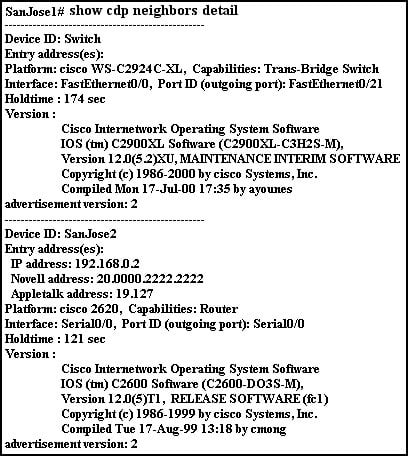
- 37.
Refer to the exhibit. Which two statements are true of the output shown? (Choose two.)
- A.
The protocol that communicated this information operates at Layer 3 of the OSI model.
- B.
The output of this command displays information about directly connected Cisco devices only.
- C.
The switch is attached to the SanJose1 FastEthernet0/21 interface.
- D.
SanJose1 is running CDP version 12.0.
- E.
SanJose1 has two fully operational, CDP-enabled Cisco switches directly connected to it.
- F.
SanJose2 is a 2600 series router running several routed protocols.
Correct Answer(s)
B. The output of this command displays information about directly connected Cisco devices only.
F. SanJose2 is a 2600 series router running several routed protocols.Explanation
The output of this command displays information about directly connected Cisco devices only because it shows the details of the devices connected to the switch. Additionally, the statement "SanJose2 is a 2600 series router running several routed protocols" is true as it provides information about the router model and the protocols it is running.Rate this question:
-
- 38.
Which two statements describe the command ip route 192.168.7.24 255.255.255.248 192.168.7.9? (Choose two.)
- A.
A packet that is destined for host 192.168.7.30 will be forwarded to address 192.168.7.9.
- B.
The address 192.168.7.9 is the destination network for this route.
- C.
The address 192.168.7.24 is the next-hop router in this command.
- D.
This command is issued from the interface configuration mode.
- E.
This command is used to define a static route.
Correct Answer(s)
A. A packet that is destined for host 192.168.7.30 will be forwarded to address 192.168.7.9.
E. This command is used to define a static route.Explanation
The command "ip route 192.168.7.24 255.255.255.248 192.168.7.9" indicates that any packet with a destination IP address of 192.168.7.30 will be forwarded to the next-hop router at address 192.168.7.9. This command defines a static route, which is a manually configured route that remains in the routing table until it is manually removed or changed.Rate this question:
-
- 39.
Which group of commands allows a router to be administered remotely?
- A.
Line con 0 - Password Class - login
- B.
Int fa0/1 - ip add 192.168.10.1 255.255.255.0 - access-class1 in
- C.
Line vty 0 4 - password cisco - login
- D.
Int vlan 1 - ip add 192.168.10.1 255.255.255.0 - No sh
Correct Answer
C. Line vty 0 4 - password cisco - loginExplanation
The group of commands "line vty 0 4 - password cisco - login" allows a router to be administered remotely. The "line vty" command is used to configure virtual terminal lines, and the "0 4" specifies the range of virtual terminal lines to be configured. The "password" command sets the password for authentication, and "cisco" is the password in this case. The "login" command enables login authentication for the virtual terminal lines, allowing remote administration of the router.Rate this question:
-
- 40.
Which protocol is described as an enhanced distance vector routing protocol?
- A.
RIP V1
- B.
RIP V2
- C.
EIGRP
- D.
OSPF
Correct Answer
C. EIGRPExplanation
EIGRP (Enhanced Interior Gateway Routing Protocol) is described as an enhanced distance vector routing protocol. It combines the features of both distance vector and link-state protocols, providing faster convergence and better scalability. EIGRP uses a metric based on bandwidth and delay to determine the best path for routing. It also supports load balancing and allows for easy configuration and management. Overall, EIGRP is considered an advanced and efficient routing protocol.Rate this question:
-
- 41.
Why is the ip host command used to create host tables on Cisco routers?
- A.
To create static routes to specific hosts
- B.
To allow communication with other IP devices by name
- C.
To provide a meaningful name for the local router
- D.
To identify only the directly attached networks and associated hosts
- E.
To define the host devices with which the router is allowed to connect
Correct Answer
B. To allow communication with other IP devices by nameExplanation
The ip host command is used to create host tables on Cisco routers in order to allow communication with other IP devices by name. By using this command, the router can associate specific IP addresses with meaningful names, making it easier for network administrators to manage and troubleshoot network connectivity. This allows for more efficient communication and enhances network functionality.Rate this question:
-
- 42.
Refer to the exhibit. From router R1, the command telnet 192.168.11.2 is entered from privileged mode and this message displays: 00:06:45: %SYS-5-CONFIG_I: Configured from console by console 192.168.11.2 Trying 192.168.11.2 . . . Open Password required, but none set
- A.
The enable secret command is missing from R2.
- B.
The enable password command is missing from R1.
- C.
The login command is missing from the line configuration mode on R2.
- D.
The password command is missing from the line configuration mode on R2.
- E.
The no shutdown command is missing from the Serial 0/0 interface mode on R1.
- F.
The no shutdown command is missing from the Serial 0/0 interface mode on R1.
Correct Answer
D. The password command is missing from the line configuration mode on R2.Explanation
The message "Password required, but none set" indicates that a password is needed to access the device, but no password has been set. This suggests that the password command is missing from the line configuration mode on R2. The password command is used to set a password for accessing the device, and without it, the device cannot authenticate the user trying to access it via Telnet.Rate this question:
-
- 43.
Which two items can be modified by the system administrator to determine from where the Cisco IOS loads? (Choose two.)
- A.
System ROM
- B.
Startup configuration file
- C.
System image file
- D.
Configuration register value
- E.
Bootloader image file
Correct Answer(s)
B. Startup configuration file
D. Configuration register valueExplanation
The system administrator can modify the startup configuration file and the configuration register value to determine from where the Cisco IOS loads. The startup configuration file contains the configuration settings that are applied when the device boots up, and the configuration register value determines the boot process and the location from where the IOS is loaded. By modifying these two items, the system administrator can control the boot process and specify the source of the IOS image.Rate this question:
-
- 44.
What are two requirements for establishing a console communication session between a computer and a router? (Choose two.)
- A.
A console cable must be used from the console port of the router to the NIC of the computer.
- B.
A rollover cable must be used from the console port of the router to the serial port of the computer.
- C.
A default gateway must be configured on the computer.
- D.
The IP addresses assigned to the router and computer must be on the same subnetwork.
- E.
There must be a terminal emulator application on the computer.
Correct Answer(s)
B. A rollover cable must be used from the console port of the router to the serial port of the computer.
E. There must be a terminal emulator application on the computer.Explanation
To establish a console communication session between a computer and a router, two requirements are necessary. Firstly, a rollover cable must be used to connect the console port of the router to the serial port of the computer. This type of cable is specifically designed for this purpose. Secondly, there must be a terminal emulator application installed on the computer. This software allows the computer to communicate with the router through the console connection. Without these two requirements, the console communication session cannot be established.Rate this question:
-
- 45.
What is the outcome when a wireless host has a different SSID configured than the access point to which it is attempting to connect?
- A.
The access point will send the host a rejection message.
- B.
The host will be prompted for a userid and password.
- C.
The access point will send the host a challenge message.
- D.
The host will only be allowed access to the Internet.
- E.
The access point will send the host a re-authentication request message.
- F.
The host will not be allowed access to the wireless network.
Correct Answer
F. The host will not be allowed access to the wireless network.Explanation
When a wireless host has a different SSID configured than the access point it is trying to connect to, it will not be allowed access to the wireless network. This is because the SSID is used to identify and match the wireless host with the correct access point. If the configured SSID does not match the access point's SSID, the access point will not authenticate the host and deny access to the network.Rate this question:
-
- 46.
A wireless network has one access point installed. Users at some locations in the office complain that their wireless access is slow, while others say that the wireless network performance is fine. What should be done to remedy this situation?
- A.
Replace the access point.
- B.
Install another access point at another location within the office.
- C.
Upgrade the wireless NICs in the hosts that are slow.
- D.
Limit the number of wireless hosts that attach to the access point at one time.
- E.
Convert back to a wired network.
Correct Answer
B. Install another access point at another location within the office.Explanation
To remedy the situation of slow wireless access for some users, installing another access point at another location within the office would be the most appropriate solution. This will help improve the coverage and distribution of the wireless network, ensuring that users in different areas of the office have better connectivity and faster access. By adding another access point, the network capacity will be increased, reducing congestion and improving overall performance for all users. This solution addresses the specific issue of slow access in certain locations and provides a targeted solution to improve the wireless network performance.Rate this question:
-
- 47.
Which technology is primarily used for security in a wireless network environment?
- A.
SSH
- B.
WPA
- C.
SSID
- D.
CSMA/CA
- E.
CSMA/CD
Correct Answer
B. WPAExplanation
WPA (Wi-Fi Protected Access) is primarily used for security in a wireless network environment. It is a security protocol that provides encryption and authentication to secure wireless networks. WPA replaces the older and less secure WEP (Wired Equivalent Privacy) protocol. WPA uses a stronger encryption algorithm and provides better security features, such as dynamic encryption keys and message integrity checks. It helps to prevent unauthorized access, data interception, and network attacks in wireless networks.Rate this question:
-
- 48.
Which technology is primarily used in a WAN?
- A.
ARP
- B.
CDP
- C.
PPP
- D.
WEP
- E.
CSMA/CD
Correct Answer
C. PPPExplanation
PPP (Point-to-Point Protocol) is primarily used in a WAN (Wide Area Network). PPP is a data link layer protocol that provides a way to establish a direct connection between two nodes in a network. It is commonly used in WAN connections such as dial-up connections, leased lines, and DSL connections. PPP provides authentication, encryption, and compression features, making it suitable for secure and efficient communication over wide area networks.Rate this question:
-
Quiz Review Timeline +
Our quizzes are rigorously reviewed, monitored and continuously updated by our expert board to maintain accuracy, relevance, and timeliness.
-
Current Version
-
Mar 22, 2023Quiz Edited by
ProProfs Editorial Team -
Jun 14, 2011Quiz Created by
Kapper59
 Back to top
Back to top